24/7 SECURITY MONITORING
Collect. Analyze. Act.
Know what’s happening in your network, and why with Security Information and Event Management (SIEM) for small to medium-sized businesses.
Let's get started
What is Security Information & Event Management?
SIEM is a fully managed log analysis and threat detection service for security monitoring. It collects data from your endpoints, firewalls, servers, cloud apps and more, and analyzes this data to detect, investigate and help you respond to suspicious activity.
Smart Filtering
Like a security camera, Managed SIEM captures everything, but only alerts you to real threats, reducing noise so your team can focus on what truly matters.
24/7 Security Monitoring
Watches your firewalls, SaaS platforms, and endpoints 24/7 to flag suspicious activity and alert your team before threats can spread or cause serious damage.
Threat Detection
Acts as a digital logbook to help meet compliance standards. All logs are securely stored, searchable, and available on demand for audits and reviews.
Compliance Support
Delivers real-time alerts when critical threats are detected. Whether it's internal misuse or external attacks, you’ll be notified quickly so you can respond fast.
Expert Response
Keeps your security logs safe, organized, and accessible for audits, incident response, and investigations—all with encrypted retention that meets compliance needs.
228+ Google Reviews
Local businesses. Real Experiences.
Serving small and mid-sized businesses across Manitoba and Saskatchewan, we're proud to be the most-rated and a leading managed IT provider in the region.
Why SIEM? Why Now?
Cyber threats are evolving and many traditional defenses like antivirus and firewalls simply aren’t enough.
Attackers are often able to move through systems undetected for months, and by the time they're discovered, the damage is already done. Managed SIEM changes that by giving you real-time visibility across your entire network, helping detect threats early through log correlation and behavioral analysis. As the cost of data breaches climbs, more cyber insurance providers are requiring businesses to have centralized security log monitoring and threat detection in place (like Managed SIEM) before issuing or renewing policies. It’s not just smart security, it’s often a requirement for doing business today.
Why 365 Technologies?
- 205+ five-star reviews from local businesses
- Trusted Huntress partner for advanced security tools
- Local support with quick response and no call center runaround
- Flat-rate pricing and clear communication
Let's build your security plan
Book your FREE 15-minute call to see how we can help
Your Best Cybersecurity Strategy is a Layered Defence
A single solution isn't enough. Discover how our layered cybersecurity offerings work together to protect every angle of your business.
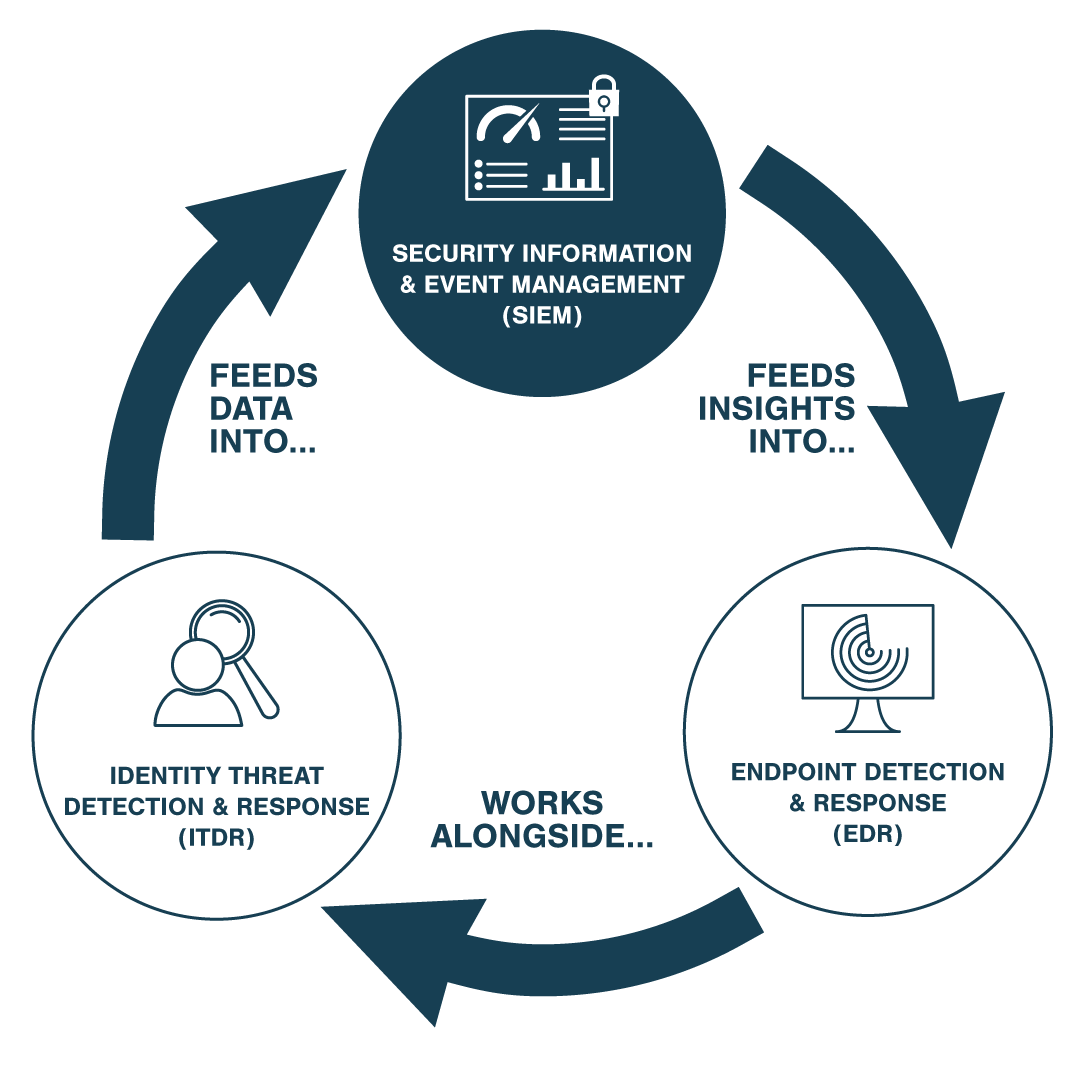
Endpoint Detection & Response (EDR)
Stops threats at the source by detecting, isolating, and removing cyberattacks before they impact your devices or data.
Identity Threat Detection & Response (ITDR)
Protects employee identities by detecting misuse, stopping credential theft, and preventing identity-based attack spread.
Ready to get started?
Book your free, no-pressure call and find out how 365 Technologies can help your business

