365 Technologies: Blog
Technology provides a competitive advantage when implemented properly. Keeping up with the latest trends is not easy. On this page we will provide you with unbiased answers to common questions we receive. This will ensure you get the information you are looking for to make sound decisions. If there is something that you would like answers to, but do not see it below, let us know and we will add it.
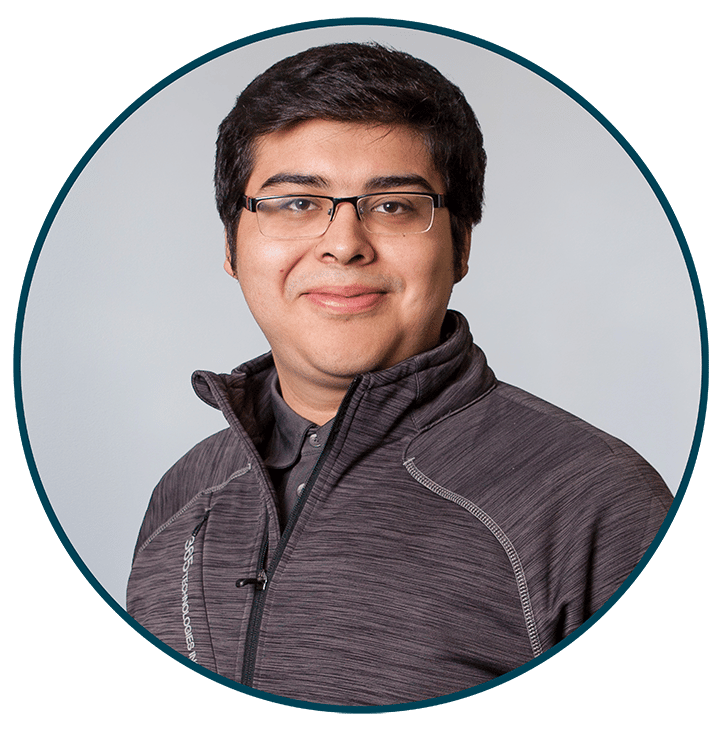
Meet Bryan Suarez, Service Technician
Bryan Suarez is one of 365 Technologies’ Service Technicians, putting him on the front line of client support each and every day.
Read MoreWestern Canadian Businesses Face Stricter Cybersecurity Insurance Requirements
Over the past few months, businesses have seen stricter liability insurance questionnaires that can frustrate their business processes.
Read MoreProfessional Computer Services In Saskatoon
365 Technologies provides computer services and computer support for organizations throughout Saskatoon.
Read MoreWhat You Need to Know About Microsoft 365 Price Increases
Microsoft is announcing the first price increase in its commercial Office 365 and Microsoft 365 subscriptions.
Read MoreOutsourced IT Advisors In Winnipeg & Western Canada
365 Technologies provides outsourced IT advisors for organizations throughout Winnipeg, Saskatoon and Regina.
Read MoreRecent Posts
How can we help?
Whether you need immediate help with an IT issue or want to discuss your long-term IT strategy, our team is here to help.
Call us at (204) 336-6518 or complete the form below and we'll help in any way we can.
"*" indicates required fields
Categories
- 365 News
- Business Talk
- Cloud
- Culture
- Cybersecurity
- Disaster Recovery
- eBooks
- Green Technology
- Hardware
- IT Best Practices
- IT Managed Services
- IT Security
- Microsoft 365
- Microsoft Bookings
- Microsoft Forms
- Microsoft OneDrive
- Microsoft Teams
- Ransomware
- Remote Working
- Software
- Tech Articles
- Video Library